In the beginning of 2009, there was a sudden increase in new form of malware being distributed. The bad guys are now getting smarter by the day, giving rise to a new breed of attacks being carried out. All the attacks have one common thing though - they exploit victims paranoia for malware !
Scareware
Almost every month there is a new variant of these so called security or Antivirus programs. These fake security programs pretend to do a scan of your system and claim that the machine is infected with lot of malware, when the fact is that there is none ! Some of the screens shown are so convincing that any one not having an antivirus will easily fall for it.
They all boast the WinXP/Vista look and feel. While some of them will trick you into downloading more malware, others will try to scare you into spending $30-80 to buy fake protection. They also supply the Visa, MasterCard and PayPal payment mechanisms that enable consumers to pay.
Ransomware
This takes fake security programs to the next level. Now apart from those irritating screens that show that the machine is infected, the malware locks and prevents other programs from running including Task Manager, Command Prompt or other system and office applications. There are even some variants that encrypt all office files stored on the system. Now the user is forced into paying up for using his own machine :o !
But who said ransomeware was limited to only forcing user to buy fake programs ?! Welcome SMS Ransomeware :) .. While some of this family of malware lock the desktop, others take control of the mouse pointer preventing you from clicking anywhere else (how irritating :/ !) except for a window that requires a code to be entered. The victim is then prompted to send a premium SMS to a specified number to receive the unlock code.
SEO (Search Engine Optimization) Attacks
This attack is carried out by exploiting the way search engines work. The bad guys create different web pages and fill them with words and phrases that are popular search queries, such as "France Airline crash" or "American Idol winner" or "Conficker" for that matter. Next they hack into a popular, legit website using XSS (read Cross Site Scripting) and insert small JavaScript that redirects the browser to their web page. This is added on as many pages of the compromised high-traffic site as they can. This is where the SEO kicks in and starts ranking web pages and prioritizing search results, based on relevance. Now along with the results for popular websites, the bad guys page also turns up. Anyone who clicks on the bad links ends up with Malware !
You might think that all this dirty work might be some script kiddie sitting somewhere in Russia wanting to earn some quick bucks. But that's not all that it is to this story - there a whole bunch of underground syndicates running these operations !! There is an excellent article posted by Byron Acohido on his blog regarding how the bad guys are making profit out of this whole fake programs thing ! Now thats some real scareware ;)
Tuesday, June 23, 2009
Friday, June 12, 2009
100,000 websites wiped off !
In what appears to be a zero-day exploit on HyperVM virtualization software, the attacker managed to wipe off data of 100,000 websites hosted by company called Vaserv. This software was developed by a company called LxLabs which is based out of Bangalore. HyperVM is a very popular software and used by many companies.
Vaserv suspects that the attacker was able to gain "root" access by exploiting the 0-day vulnerability and then deleted files from the system. On the contrary a anonymous post somewhere suggests it was something else. The post contains all the gory details of how the attackers went about screwing up the systems. I can't believe that there are sadistic people in this world today that enjoy giving commands like "rm -rf *". The extent of the damage is still not completely know and it seems the billing systems were also 0wned ! Apparently, details of the vulnerability were known to LxLabs 2 weeks before this incident took place.
Worst part is that 50% of the customers who were hosted on the compromised ISP didn't have backups (since they had subscribed to un-managed service) so god knows if they will ever get the data back ! A lesson to be learned here for everyone - "If it’s your data, back it up!" Can't rely on others to do it for you. This is like the worst kind of attack that anyone can get and just shows how critical it is to secure the infrastructure especially for big ISP's.
As if this was not enough, the founder of LxLabs committed suicide on the next day of Vaserv reporting this incident. Now people all over seem to be linking these two things together, but I doubt that's the case. Anyways, may his soul rest in peace!
Ref: http://www.techworld.com/security/news/index.cfm?newsID=117342&pagtype=samechan
Vaserv suspects that the attacker was able to gain "root" access by exploiting the 0-day vulnerability and then deleted files from the system. On the contrary a anonymous post somewhere suggests it was something else. The post contains all the gory details of how the attackers went about screwing up the systems. I can't believe that there are sadistic people in this world today that enjoy giving commands like "rm -rf *". The extent of the damage is still not completely know and it seems the billing systems were also 0wned ! Apparently, details of the vulnerability were known to LxLabs 2 weeks before this incident took place.
Worst part is that 50% of the customers who were hosted on the compromised ISP didn't have backups (since they had subscribed to un-managed service) so god knows if they will ever get the data back ! A lesson to be learned here for everyone - "If it’s your data, back it up!" Can't rely on others to do it for you. This is like the worst kind of attack that anyone can get and just shows how critical it is to secure the infrastructure especially for big ISP's.
As if this was not enough, the founder of LxLabs committed suicide on the next day of Vaserv reporting this incident. Now people all over seem to be linking these two things together, but I doubt that's the case. Anyways, may his soul rest in peace!
Ref: http://www.techworld.com/security/news/index.cfm?newsID=117342&pagtype=samechan
Labels:
Cyber Crime
Thursday, June 11, 2009
XM Personal FTP Server vulnerability
Recently I discovered a Denial-of-Service vulnerability in XM Personal FTP Server 5.7. This is a easy to use FTP Server application which can help you create a FTP server really fast without any complex configuration.
This vulnerability was actually discovered in May. Despite of trying multiple times to contact the author of this software, he did not respond to my communication. So eventually I decided to post the details of the vulnerability as well as the PoC on Bugtraq.
The vulnerability exists because the application fails to handle arguments passed to some of the standard FTP commands such as HELP and TYPE. This vulnerability was actually discovered accidentally when I was trying to figure out how to use fuzzing tools ! :) ... The tool used for this was FTP Fuzzer 1.0 from Infigo which a nice tool for fuzzing. This is just a DoS vulnerability and remote code execution is not possible. For some strange reason Security Focus has mentioned that remote code execution is possible, but I don't think so.
Some time I will make an article on Fuzzing. Its pretty interesting concept and in fact I am also writing a protocol fuzzer. Hopefully it should be done soon !
Details of the vulnerability available at -
http://www.securityfocus.com/bid/35239
http://secunia.com/advisories/35271/
This vulnerability was actually discovered in May. Despite of trying multiple times to contact the author of this software, he did not respond to my communication. So eventually I decided to post the details of the vulnerability as well as the PoC on Bugtraq.
The vulnerability exists because the application fails to handle arguments passed to some of the standard FTP commands such as HELP and TYPE. This vulnerability was actually discovered accidentally when I was trying to figure out how to use fuzzing tools ! :) ... The tool used for this was FTP Fuzzer 1.0 from Infigo which a nice tool for fuzzing. This is just a DoS vulnerability and remote code execution is not possible. For some strange reason Security Focus has mentioned that remote code execution is possible, but I don't think so.
Some time I will make an article on Fuzzing. Its pretty interesting concept and in fact I am also writing a protocol fuzzer. Hopefully it should be done soon !
Details of the vulnerability available at -
http://www.securityfocus.com/bid/35239
http://secunia.com/advisories/35271/
Labels:
Vulnerabilty Disclosure
Friday, June 5, 2009
The long and short of it..
Do you get frustrated sending huge links to people only to find out that they don't work because it got cut due to text wrapping :( ? Well, URL "shortners" are the thing you should be looking for. These websites claim to make the url small so that you can have a customized url and don't have to send the whole long thing to your friends. So, services like "bit.ly", "tr.im" and "notlong.com" are a lot popular with social networking sites such as twitter where there is a character limit to what you can post. The best part is - its free !
So what's the big deal you may say. The thing is that the way these URL shortening services work is by redirection and this conceals the URL of the actual website you are landing on to. So, someone could send you a link that says "tinyurl.com/bunchofflowers" and actually send you to "www.evilperson.com/go/down/the/drain/looser.html?format=1". Security is a big concern here and before you know it, you may get redirected to a website that hosts some browser exploit to download malware on your system.
Moreover the reliability is also a issue. For the link to work, now the destination webserver as well as the re-director should be up and running. With these services being given out for free I can imagine the kind of load these servers must be receiving. Bit.ly CEO claims they receive 100 million hits per week** !!! :o
Solution ? - "For every new invention, there is a equal and opposite invention".. welcome "http://longurl.org/". It will expand and show you every small url that you type in - Smart eh ?! ;) So, next time you receive such shortened links use this website and be sure that you are getting redirected to the correct website.
** Ref: http://www.google.com/hostednews/ap/article/ALeqM5hAbmy1E7zWJIkAp74Nt0LFzP5KtQD98HBJJG3
So what's the big deal you may say. The thing is that the way these URL shortening services work is by redirection and this conceals the URL of the actual website you are landing on to. So, someone could send you a link that says "tinyurl.com/bunchofflowers" and actually send you to "www.evilperson.com/go/down/the/drain/looser.html?format=1". Security is a big concern here and before you know it, you may get redirected to a website that hosts some browser exploit to download malware on your system.
Moreover the reliability is also a issue. For the link to work, now the destination webserver as well as the re-director should be up and running. With these services being given out for free I can imagine the kind of load these servers must be receiving. Bit.ly CEO claims they receive 100 million hits per week** !!! :o
Solution ? - "For every new invention, there is a equal and opposite invention".. welcome "http://longurl.org/". It will expand and show you every small url that you type in - Smart eh ?! ;) So, next time you receive such shortened links use this website and be sure that you are getting redirected to the correct website.
** Ref: http://www.google.com/hostednews/ap/article/ALeqM5hAbmy1E7zWJIkAp74Nt0LFzP5KtQD98HBJJG3
Labels:
Web Attacks
Tuesday, June 2, 2009
You've g0t Ma1L
Recently I received a funny mail about some missing parcel from "United Parcel Service of America" ! At first, it seem to a very legitimate mail and didn't appear to be a obvious spam email. But unfortunately for the sender of the mail, I knew that I had not ordered any parcel so my hacker senses were soon tingling :) ..

[ Fig 1 - Mail about some parcel not being delivered ]
A closer look at the mail reveals some interesting aspects of the spammer. Firstly there are no obvious spam symptoms and the sender also looks legit. Then the body is also well structured making it look authentic. So, I went ahead (knowing I had a Symantec AV installed & updated) and extracted the contents of the attachment to a folder. To my surprise, it did extract without any warnings.
As a person who eats malware for breakfast and lunch, I have one good habit of un-checking the "Hide extensions for known file Types" option in windows explorer (Tools >> Folder Options >> View) on all systems that I work with. Some how I never understood why this option is there in the first place and that too checked by default for WinXP installations. Anyways, to make matters worse Windows explorer conveniently prevents the full name from showing up (since its a long name) making it look like a nice excell file to open. By now, I am sure any innocent user would have fallen prey to the sender and executed this file.
After selecting the file, the full name shows up - "UPS_DOC_986001.exe". Gotcha ! Now, since when did invoice copies start getting distributed in the form of executables ?! A quick virustotal scan identifies the Trojan as Win32/Bredolab [symantec]. Even as I uploaded the file to virustotal, my symantec AV didn't raise any alarms which is a bit unusual since its the first one to jump on any file I attempt to view. Bredolab is a downloader type of trojan which has been discovered recently. Some of the variants of this type of Postal mails are known to download Fake AV programs and other malicious files.
Such method of distributing malware is not new. Some older versions referring to "Western Union" instead of UPS have been circulating for some time now indicating that this mail could also be from the same malware authors. So, be careful with attachments when you receive mails from unexpected or unknown sources and don't forget to change the windows explorer file extension settings!
[ Fig 1 - Mail about some parcel not being delivered ]
A closer look at the mail reveals some interesting aspects of the spammer. Firstly there are no obvious spam symptoms and the sender also looks legit. Then the body is also well structured making it look authentic. So, I went ahead (knowing I had a Symantec AV installed & updated) and extracted the contents of the attachment to a folder. To my surprise, it did extract without any warnings.
As a person who eats malware for breakfast and lunch, I have one good habit of un-checking the "Hide extensions for known file Types" option in windows explorer (Tools >> Folder Options >> View) on all systems that I work with. Some how I never understood why this option is there in the first place and that too checked by default for WinXP installations. Anyways, to make matters worse Windows explorer conveniently prevents the full name from showing up (since its a long name) making it look like a nice excell file to open. By now, I am sure any innocent user would have fallen prey to the sender and executed this file.
After selecting the file, the full name shows up - "UPS_DOC_986001.exe". Gotcha ! Now, since when did invoice copies start getting distributed in the form of executables ?! A quick virustotal scan identifies the Trojan as Win32/Bredolab [symantec]. Even as I uploaded the file to virustotal, my symantec AV didn't raise any alarms which is a bit unusual since its the first one to jump on any file I attempt to view. Bredolab is a downloader type of trojan which has been discovered recently. Some of the variants of this type of Postal mails are known to download Fake AV programs and other malicious files.
Such method of distributing malware is not new. Some older versions referring to "Western Union" instead of UPS have been circulating for some time now indicating that this mail could also be from the same malware authors. So, be careful with attachments when you receive mails from unexpected or unknown sources and don't forget to change the windows explorer file extension settings!
Labels:
Malware
Monday, June 1, 2009
Dawn of the Downl0ad3rs
So what are Trojan downloaders ?? To say in short "Malware that is designed to download more malware" (duh !?). Actually, over the years these downloaders have evolved a lot and today they represent a major chunk of the malware family.
So, what is the sole purpose of these so called Trojan downloaders - "To download more nasty stuff on the affected machine" (duh again !?) Yes.. much more than that. They are designed to be lightweight, stealth, evade Intrusion Prevention devices and more over give the attacker full control over what gets downloaded when !!
Typically, as soon as a downloader is executed on a system. It will contact a website (generally hard coded domain names) and wait for the response. But unlike a normal webservers response, what actually comes is a list of URL's to download more bad stuff from -
So, what is the sole purpose of these so called Trojan downloaders - "To download more nasty stuff on the affected machine" (duh again !?) Yes.. much more than that. They are designed to be lightweight, stealth, evade Intrusion Prevention devices and more over give the attacker full control over what gets downloaded when !!
Typically, as soon as a downloader is executed on a system. It will contact a website (generally hard coded domain names) and wait for the response. But unlike a normal webservers response, what actually comes is a list of URL's to download more bad stuff from -
[ Fig 1 - Typical Trojan downloader webserver response ]
So, now the attacker who owns the server can control what gets downloaded on the affected system. He can change the files or links whenever he wants to. All the downloader has to do is fetch all the files listed in the URL and execute them. But thats not all, how about some obfuscation to trick our good ol' Intrusion Detection/Prevention devices (IDS/IPS) !?
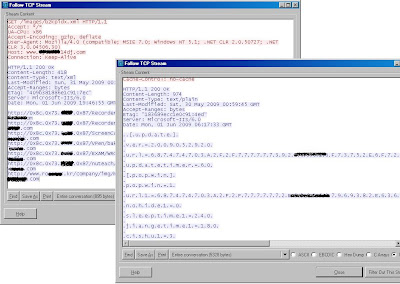
[ Fig 2 - Encoded or obfuscated response ]
In what may seem like bunch of garbage characters, is actually a hex coded or obfuscated data to keep the good guys at bay. The webserver in this case gets even more sophisticated, scripting other activities for the downloader Trojan running on the affected machine!

[ Fig 3 - Using image name for downloading ]
Another trick is to use image names for downloading malware. At first it appears to be a harmless image download, but actually is a executable file ! Wireshark is smart enough to detect that its not a image, but can your IDS/IPS do it ?!
Ultimately a whole bunch of crap - from Worms/Trojans to Fake AV programs to malicious .pdf and .swf files can get downloaded on your system. So, be careful and keep your AV's updated, you never know what a small exe could do to your system !
So, now the attacker who owns the server can control what gets downloaded on the affected system. He can change the files or links whenever he wants to. All the downloader has to do is fetch all the files listed in the URL and execute them. But thats not all, how about some obfuscation to trick our good ol' Intrusion Detection/Prevention devices (IDS/IPS) !?
[ Fig 2 - Encoded or obfuscated response ]
In what may seem like bunch of garbage characters, is actually a hex coded or obfuscated data to keep the good guys at bay. The webserver in this case gets even more sophisticated, scripting other activities for the downloader Trojan running on the affected machine!
[ Fig 3 - Using image name for downloading ]
Another trick is to use image names for downloading malware. At first it appears to be a harmless image download, but actually is a executable file ! Wireshark is smart enough to detect that its not a image, but can your IDS/IPS do it ?!
Ultimately a whole bunch of crap - from Worms/Trojans to Fake AV programs to malicious .pdf and .swf files can get downloaded on your system. So, be careful and keep your AV's updated, you never know what a small exe could do to your system !
Labels:
Malware
WeLc0m3
.. to the Hypersecurity Blog. This blog is about my research in the field of Network and Computer Security. So hop on and I will show you how deep the rabbit hole goes in Alice's computer'land.. :)
Labels:
About this blog
Subscribe to:
Posts (Atom)






