Posting after a long time.. was quite busy with some presentations to make as well as with my Protocol Fuzzer script which should be ready soon.
Anyways, the Zeus Botnet has been around for quite some time now and has gained some attention with its Internet Banking password stealing campaigns and Zeus Crimeware Kit ! Recently I received a sample which happened to be one of the Trojans belonging to this family.
“uk.exe” as it being distributed around in the wild initially seemed something else as VirusTotal results reported a rather poor detection percentage by AV vendors and also a different name like Trojan.Meredrop or Bancos.lgi. At the time of this analysis, only 2 of the major five AV companies were able to detect this Trojan and Microsoft reports suggested it as a downloader.
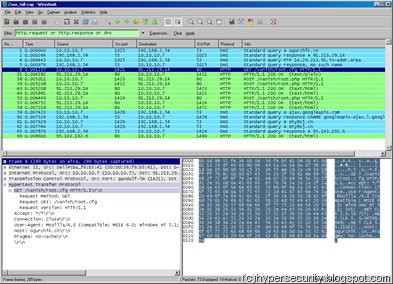
But, when I started up with my usual dynamic analysis, things were a little different. I had no idea that I was dealing with Zeus Botnet Trojan. This Trojan has a root kit functionality and it injects itself into one of windows processes to avoid detection. As soon its executed, the orginal process (uk.exe) exited and soon the Trojan became part of svchost.exe as expected. It then connected to “ogurchik.cn” like any typical downloader over HTTP.
As I was looking at wireshark trying to search patterns to write IPS signature, I noticed that everything was encrypted :( A little disappointed, I started digging in deeper looking at File/Registry changes done by the malware to see if I could locate the downloaded stuff on the disk. Even that too was encrypted and file locked by the Trojaned process itself. So, as usual when nothing works google does :) .. searching for “ogurchik.cn” directly landed me to zeustracker.org website and I realized that I was dealing with something more sinister than just a downloader.
After reading an excellent article at Threatexpert blog on the Zeus Botnet, I knew that I was dealing with “variant 4” of the Zeus Botnet and that the encrypted communication is nothing but the configuration file of the Bot. Luckily I got hold of the Zeus Decryptor tool so I didn't have to re-invent the wheel. The encryption is done using RC4 algorithm and the funny part is that the 256-bit key is stored within the Trojan exe when its built. So for the Decryptor tool to work, it has to run on the same infected machine so that it can extract the key from the memory of the Trojaned process.
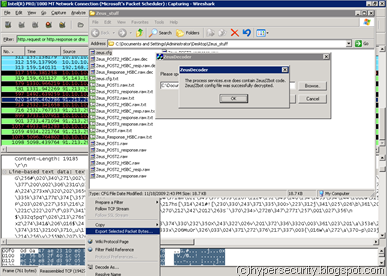 Fig2 : Dumping raw data from Wireshark / Decryptor in Action
Fig2 : Dumping raw data from Wireshark / Decryptor in Action
After dumping raw data from the HTTP Response into file (zeus.cfg.raw), I ran the decryptor tool to get the clear text data and was shocked to see js code in it ! When I was reading more on the Zeus functionality, I was amazed at one of the Trojans capability and that was to intercept & inject HTML code in Browser in real-time ! So, I decided to play around more with the Trojan hoping to see the password stealing process in action. After going through the fairly elaborate Java code, I figured out that it was designed to manipulate code for banking sites belonging to HSBC, Abbey Santander, Alliance & Leicester and NatWest banks – all UK based Internet banking sites.
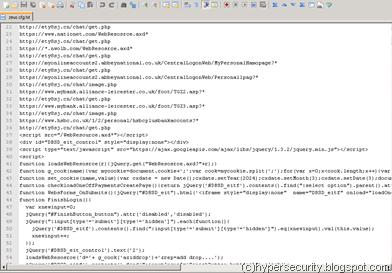 Fig3: The Zeus configuration file
Fig3: The Zeus configuration file
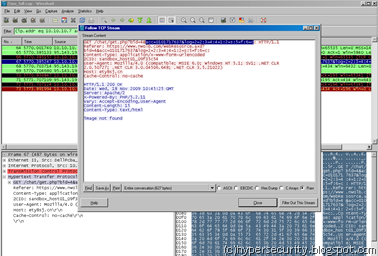
So, I opened the NatWest website and entered some fake details for all the fields and voila ! .. Apart from the encrypted traffic, there was a HTTP request to “ety8sj.cn” submitting all the data captured in clear text ! There it was – all the credentials nicely packaged along with “ZCID” (Zeus ID) which was my machine name followed by random string. I wonder why the malware authors decided to keep this part in clear text, they might as well have had used encryption for this too – but hey, it definitely made my life easier since I could now write a IPS signature for it ! :)
Fig4: Stolen credentials being submitted to the attacker
But the ability to inject code and manipulate data in the Browser was just amazing ! I mean who thought of this thing – it just defeated everything - SSL, Secured Login everything ! As If that was not enough - it detects the virtual keyboard in use and starts taking screenshots leaving end user completely helpless !
At this moment there are Zeus Kits being sold in the wild for anywhere between $400 to $800 and mind you these are sophisticated kits with a proper User Interface and statistics logging which allow you to completely customize the Trojan as per the needs. Some guys are also selling “Zeus as a service” giving control of their botnet on rent for a few days ! :o Since each binary of the Trojan generated from the kit is designed to have different code, the criminals can virtually churn out thousands of such Trojans and that explains the poor detection rate by the AV companies.