Wednesday, December 30, 2009
Digging deep into BlackHat SEO - Part2
Thursday, December 24, 2009
Digging deep into BlackHat SEO – Part1
It was used before for tragic news and has been seen once again now when actress Brittany Murphy passed away over the last weekend. Cybercriminals have been very effectively using SEO techniques to download malware on users machines who are trying to browse Internet looking for latest breaking news.
A simple Google search for “Brittany Murphy death” reveals some interesting search results. After the first two-three valid results, there are some mysterious links that at first seem very valid based on the preview text you see in the results.
There is no way any average user can figure this out but when you actually click on one of such links, it takes you to some completely different URL and often through multiple redirects.
This is all done using Search Engine Optimization (SEO) techniques. The bad guys first create a page and dump all the popular sentences surrounding a breaking news like – “Airline crash” or “Michael Jackson death” onto that page. They also inject an iframe on the same page that will have one or more redirects to a malicious web page. Then using special SEO tools like XRumer they increase their page ranking by spamming their URL all over the internet.
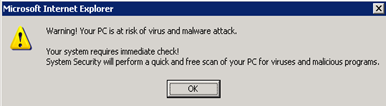
When you click on one such poisoned search result, suddenly out of no where there will be a windows pop-up alert on your screen -
Ultimately you end up landing on a page that first seems like an Antivirus which is scanning your local machine but is in fact a very cleverly designed web page.
So depending on which OS you are running, the malicious webserver shows you a corresponding look and feel type of Antivirus program. This one above shows a Vista/Win7 look and feel to it where as if you are running WinXP you get this -
If you look closely, it is completely designed to trick a user into believing that a Antivirus is scanning the PC. If you are an average Internet user, you won’t even realize that this is being rendered through Internet Explorer ! That is some clever use of HTML and JavaScript code ;)
At this point, irrespective of where you click, you will be prompted to download and install a setup file which is nothing but a downloader Trojan. It downloads Rogue Antivirus program which not only have a look and feel of popular AV programs but also have funky names like “Antivirus 2010” or “PC Protect 2010”. But before you can say clean, it will prompt you for registration which can be anywhere from 30$ to 80$ :P !
This trick of threatening the a victim by showing how infected his PC is, works out rather well. A lot of not-so-tech-savvy people fall for such kind of tricks and the bad guys seem to be earning a lot. The Rogue AV products keep changing their names and so do the various domains that host these malicious pages. This has been one of the very popular attack vector for malware distributers in 2009.
In the next part I will show you what all things go behind the scene in these type of attacks.
Stay tuned and Merry Christmas ! :)
Wednesday, December 2, 2009
NetBIOS Spoofing
The other day I came across a post at skullsecurity.org that spoke about an interesting way of using NetBIOS name service for doing MiTM attack. The author showed how his tool nbpoison could be used to inject false NetBIOS information on the wire and spoof other hosts.
This is very interesting form of doing MiTM as there is no arp-spoofing involved and that is good, since every Tom, Dick and Harry’s device in the network today detects/blocks arp-poisoning kind of attacks. Also, arp-spoofing is way to noisy and can easily give away attackers presence in the network. Not to mention that its a old-school attack that has been there for quite some time now.
So, I decided to explore this and have some fun using the nbtools and figure out what all attacks can be made possible in my Lab. I have in all 3 machines in my lab - 2 WinXP Hosts and 1 Linux host which acts as the gateway for the windoze boxes. As the author has mentioned, this attacks are more useful in hotels or conferences where there are internet kiosks with captive portal authentication mechanisms.
Scenario 1: DNS Choking
This attack is useful when, for some reason, DNS server on a network is not reachable. There could be multiple possibilities -either uplink of the switch you are connected to is (purposely) physically disconnected or network/firewall miss-configuration or DNS server/service itself is down. Even some captive portals prevent access to any resources before you authenticate. So, if the DNS server is not available, as a last resort, Windoze will fall back to NetBIOS name resolution and this is where we can 0wn the box.
So, as you can see, webserver on the Linux box was used to host the fake page which could have been anything from fake captive portal logins to fake Gmail login page to trick the user into entering his credentials. In the above scenario, I had blocked all connections from the victims (10.10.10.7) machine using iptables on the gateway (Linux Box). FYI, the nbpoison tool can be run on any machine and need not be on the gateway.
Scenario 2: Abusing WPAD Requests
This type of attack is useful when browsers have the “Automatically detect settings” enabled in the “LAN Settings” menu. IE and Firefox both have this setting in order enable network administrators to automatically configure proxy settings. This is made possible using WPAD (Web Proxy Auto Discovery) protocol which also uses NetBIOS requests to look for the “wpad.dat” file. This is nothing but a simple plain-text configuration file that tells the browser which proxy to connect to for browsing the internet.
So, here we use the famous “sslstrip” to force HTTPS connection to HTTP and sniff passwords in clear text. Like before, we use the webserver on the Linux box to host the wpad.dat file which redirects the victims browser to sslstrip (running on port 8080) and we get to see all the good stuff :) !
The possibilities in this scenario are endless. We could use our own proxy, something like Paros to completely manipulate the victims browsing experience. But I will leave all the evil thinking to the reader as an exercise ;)
** DISCLAIMER: This is meant as a pure instructional tutorial. I am not responsible for the damages caused by any script-kiddies stupidity or lack of understanding thereof. No harm in any form was caused to anybody in the making of this tutorial.