It was used before for tragic news and has been seen once again now when actress Brittany Murphy passed away over the last weekend. Cybercriminals have been very effectively using SEO techniques to download malware on users machines who are trying to browse Internet looking for latest breaking news.
A simple Google search for “Brittany Murphy death” reveals some interesting search results. After the first two-three valid results, there are some mysterious links that at first seem very valid based on the preview text you see in the results.
There is no way any average user can figure this out but when you actually click on one of such links, it takes you to some completely different URL and often through multiple redirects.
This is all done using Search Engine Optimization (SEO) techniques. The bad guys first create a page and dump all the popular sentences surrounding a breaking news like – “Airline crash” or “Michael Jackson death” onto that page. They also inject an iframe on the same page that will have one or more redirects to a malicious web page. Then using special SEO tools like XRumer they increase their page ranking by spamming their URL all over the internet.
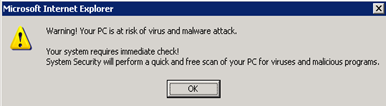
When you click on one such poisoned search result, suddenly out of no where there will be a windows pop-up alert on your screen -
Ultimately you end up landing on a page that first seems like an Antivirus which is scanning your local machine but is in fact a very cleverly designed web page.
So depending on which OS you are running, the malicious webserver shows you a corresponding look and feel type of Antivirus program. This one above shows a Vista/Win7 look and feel to it where as if you are running WinXP you get this -
If you look closely, it is completely designed to trick a user into believing that a Antivirus is scanning the PC. If you are an average Internet user, you won’t even realize that this is being rendered through Internet Explorer ! That is some clever use of HTML and JavaScript code ;)
At this point, irrespective of where you click, you will be prompted to download and install a setup file which is nothing but a downloader Trojan. It downloads Rogue Antivirus program which not only have a look and feel of popular AV programs but also have funky names like “Antivirus 2010” or “PC Protect 2010”. But before you can say clean, it will prompt you for registration which can be anywhere from 30$ to 80$ :P !
This trick of threatening the a victim by showing how infected his PC is, works out rather well. A lot of not-so-tech-savvy people fall for such kind of tricks and the bad guys seem to be earning a lot. The Rogue AV products keep changing their names and so do the various domains that host these malicious pages. This has been one of the very popular attack vector for malware distributers in 2009.
In the next part I will show you what all things go behind the scene in these type of attacks.
Stay tuned and Merry Christmas ! :)





No comments:
Post a Comment