Nothing new, It has happened in the recent past as folks at Zscaler had pointed out. But this time its not the malware itself, but part of its configuration and components being hosted on Google code servers. For those who don’t know Google code is a free, Web based platform that provides tools and resources to developers interested in working on Google-related open source software projects or projects that leverage Google services.
[Microsoft : Win32/Mofksys.A] (rather difficult to pronounce) is a worm type of Malware that spreads via network shares, removable drives and by email. While analyzing it today, I found out that It is using *.googlecode.com for hosting its malware components. And its not just a single project site that is being used - there are multiple projects hosting various components of this malware !
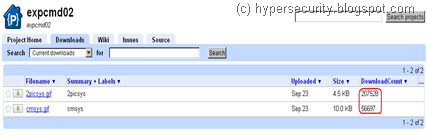
Once executed, apart from doing all the nasty stuff, one of the activity of this worm is to fetch its configuration and component files. These are being stored as .gif files on Google Code servers.
Despite of what Google claims about protecting users from malware being hosted on their servers, I found that this malware author seems to be using it for quite some time now !
Some of the entries date back to as old as 16th Oct 2009, which is when this Project was created ! It means that the worm has been around for almost a year now. No wonder these files have been downloaded so many times !
Following projects are being used by this malware -expcmd01.googlecode.com
expcmd02.googlecode.com
expcmd03.googlecode.com
expeml04.googlecode.com
expcmd04.googlecode.com
Based on the Project naming convention - “cmd” and “eml” could be for commands and email template respectively. While it is too early to comment if this is a new kind of BotNet, but this could be another smart way to use Google Code servers for C&C communications just like we saw Twitter being used as C&C sometime back. Haven’t had a detailed look at the downloaded files but they have names like cmsys.gif, udsys.gif, 2picsys.gif and use some kind of encryption (not clear text).
Following are the md5 of the samples that seem to be using the same set of Google code Projects to download components from – ee84838421768c902690281178e7a0ce
c7dcc44cb0c3355bedff8bc7c34ab43c
Google was prompt enough to remove the Projects as soon as I reported the matter to them. So as of this writing they are no longer accessible.
Using popular public services such as Google code, Twitter, Facebook, etc.. as C&C servers is a great way of ensuring that the controls channels stay low on the radar as well as away from content filtering software thus ensuring longevity of the malware. I won’t be too surprised if this turns out to be a part of a new Bot building kit like the Zeus :P



No comments:
Post a Comment